Browsing IT Challenges: Situating Managed Service Providers Near Me
Browsing IT Challenges: Situating Managed Service Providers Near Me
Blog Article
Strategize and Range WITh Proven IT Managed Solutions Strategies
In the fast-paced landscape of modern company, the critical use of IT handled services has actually come to be a foundation for companies intending to improve functional efficiency and drive lasting development. By carrying out tested methods tailored to meet certain business demands, firms can navigate the intricacies of innovation while remaining dexterous and competitive in their corresponding sectors.
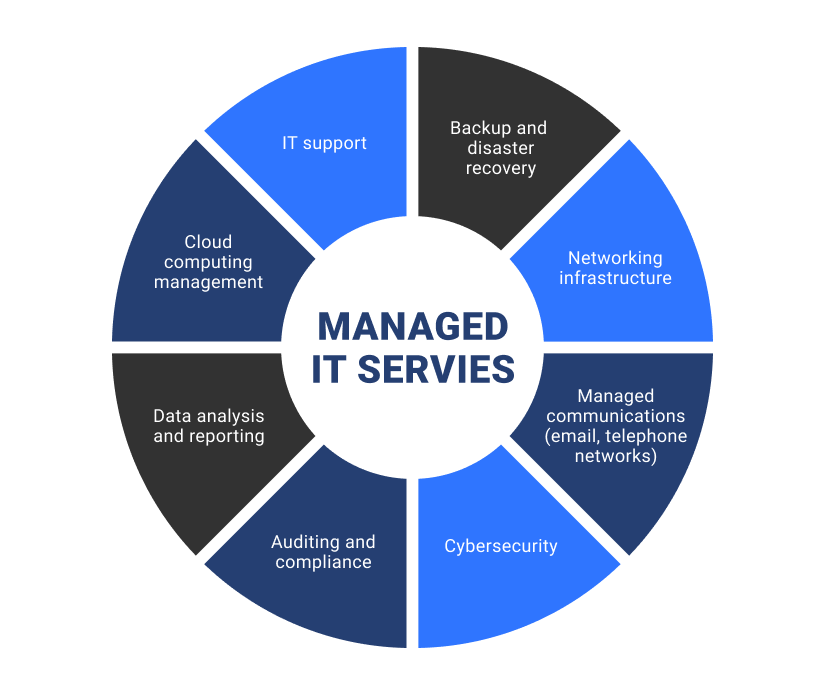
Benefits of IT Handled Solutions
Undoubtedly, the advantages of IT Managed Services are extremely important in boosting business efficiency and reducing downtime. By outsourcing IT monitoring to a specialized company, companies can touch right into a wide range of knowledge and sources that would otherwise be expensive to keep internal. One of the vital advantages of IT Handled Provider is proactive monitoring and maintenance of systems, which helps protect against potential problems before they escalate right into significant troubles. This positive approach equates into enhanced system uptime, lowered downtime, and enhanced overall performance for the company.
This ensures that businesses remain competitive in a rapidly evolving technological landscape. In final thought, the benefits of IT Managed Providers are critical in enhancing procedures, boosting effectiveness, and ultimately, driving business success.
Secret Methods for Execution
With an understanding of the considerable benefits that IT Managed Solutions offer, services can currently focus on executing vital techniques to properly integrate these solutions into their operations. One important strategy is to plainly define the range of services needed. This entails conducting a detailed evaluation of present IT facilities, recognizing pain factors, and establishing certain goals for renovation. Furthermore, businesses need to develop clear interaction networks with their taken care of company to ensure seamless partnership and timely problem resolution.
Another crucial method is to prioritize cybersecurity steps. Information violations and cyber risks pose significant threats to organizations, making security a top concern. Carrying out robust safety and security procedures, regular tracking, and prompt updates are essential actions in safeguarding delicate details and preserving company connection.
Additionally, businesses ought to establish solution level agreements (SLAs) with their handled company to specify assumptions, responsibilities, and efficiency metrics. SLAs help in setting clear standards, making sure accountability, and keeping solution quality requirements. By integrating these key approaches, organizations can take advantage of IT Managed Provider to enhance procedures, enhance effectiveness, and drive lasting growth.
Maximizing Performance Through Automation
In addition, automation makes it possible for real-time surveillance and information evaluation, supplying beneficial understandings for informed decision-making. By automating regular surveillance jobs, services can proactively resolve concerns before they intensify, reducing downtime and enhancing performance (it managed service providers). In addition, automation can promote the smooth integration of various systems and applications, enhancing collaboration and data flow throughout the organization
Ensuring Data Security and Compliance
Data safety and conformity are critical worries for businesses operating in the electronic landscape of today. With the raising volume of delicate information being kept and processed, ensuring durable safety procedures is crucial to secure versus cyber risks try these out and stick to regulative needs. Carrying out comprehensive data security techniques involves encrypting data, developing access controls, routinely updating software, and performing safety and security audits. Abiding with laws such as GDPR, HIPAA, or PCI DSS is important to stay clear of costly fines and preserve depend on with consumers. Handled IT providers play a vital function in assisting organizations browse the complicated landscape of information safety and security and conformity. They supply experience in carrying out protection methods, keeping an eye on systems for potential violations, and making sure adherence to market laws. By partnering with a reputable handled solutions provider, companies can improve their data safety pose, minimize his response risks, and demonstrate a commitment to shielding the discretion and stability of their data assets.
Scaling IT Facilities for Development
Including scalable IT framework remedies is necessary for helping with organization development and functional efficiency. As business increase, their IT needs evolve, needing framework that can adjust to raised demands effortlessly. By scaling IT facilities efficiently, organizations can make sure that their systems remain reliable, safe and secure, and performant even as work grow.
One key element of scaling IT infrastructure for development is the capability to flexibly designate sources based upon present needs. Cloud computing services, for example, offer scalability by enabling companies to readjust storage space, processing power, and other sources as needed. This elasticity makes it possible for firms to efficiently handle spikes sought after without over-provisioning sources throughout periods of reduced activity.
Additionally, executing virtualization modern technologies can improve scalability by enabling the development of virtual circumstances that can be conveniently copied or modified to fit transforming workloads - it managed service providers. By virtualizing web servers, storage, and networks, organizations can maximize source utilization and enhance IT management procedures, inevitably sustaining company development initiatives efficiently
Conclusion
In final thought, executing IT handled services can bring various advantages to a company, such as boosted performance, enhanced data protection, and scalability for growth. By adhering to vital techniques for application, using automation to maximize performance, and guaranteeing information security and conformity, organizations can much better strategize and scale their IT facilities. It is important for companies to adapt and develop with technological advancements to remain affordable in today's ever-changing landscape.
Report this page